Recently, I acquired a PlugX builder/controller. This seems to be the same as the one referred in AhnLab’s APT attacks analysis report, judging from the GUI window. I tried to use it.
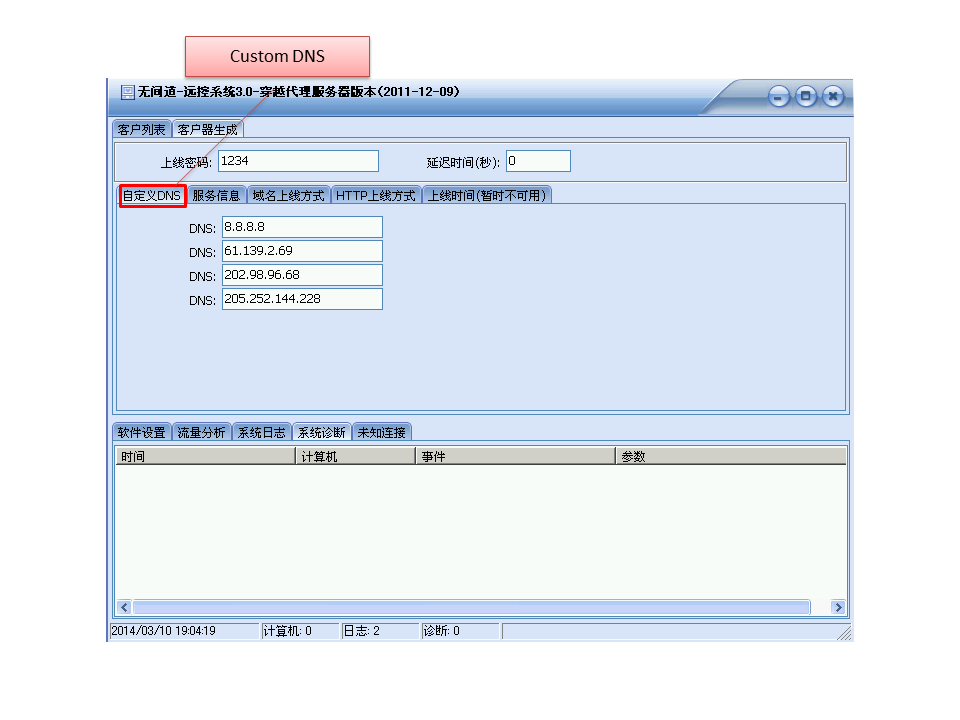
This PlugX version (we call it “TypeIII”) supports custom DNS servers.
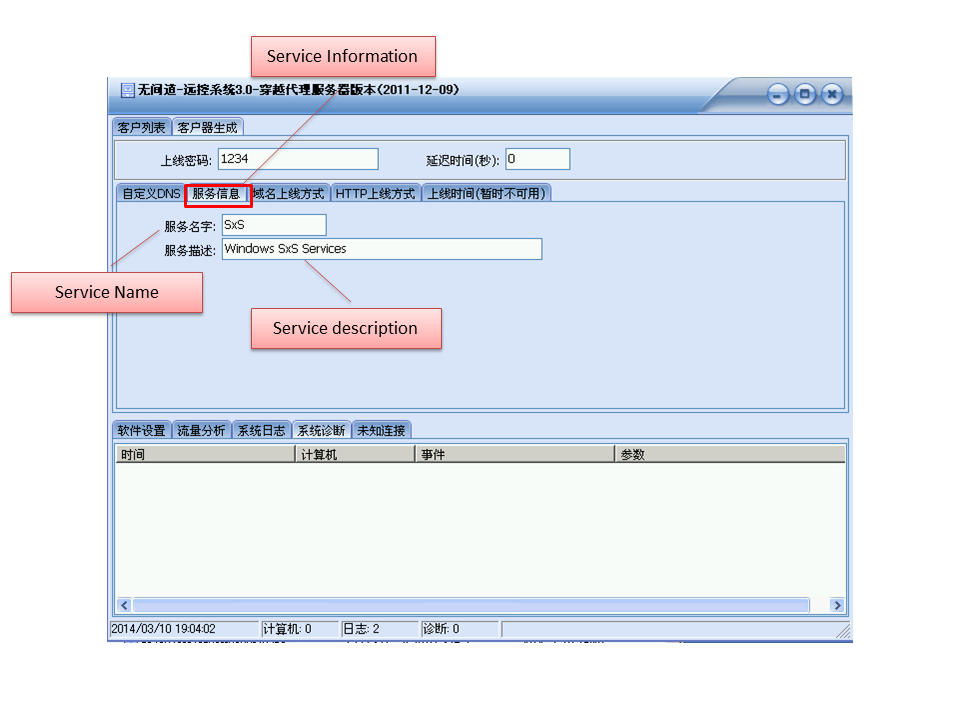
The service information like service(or dll) name and service description is simpler than Type I/II.
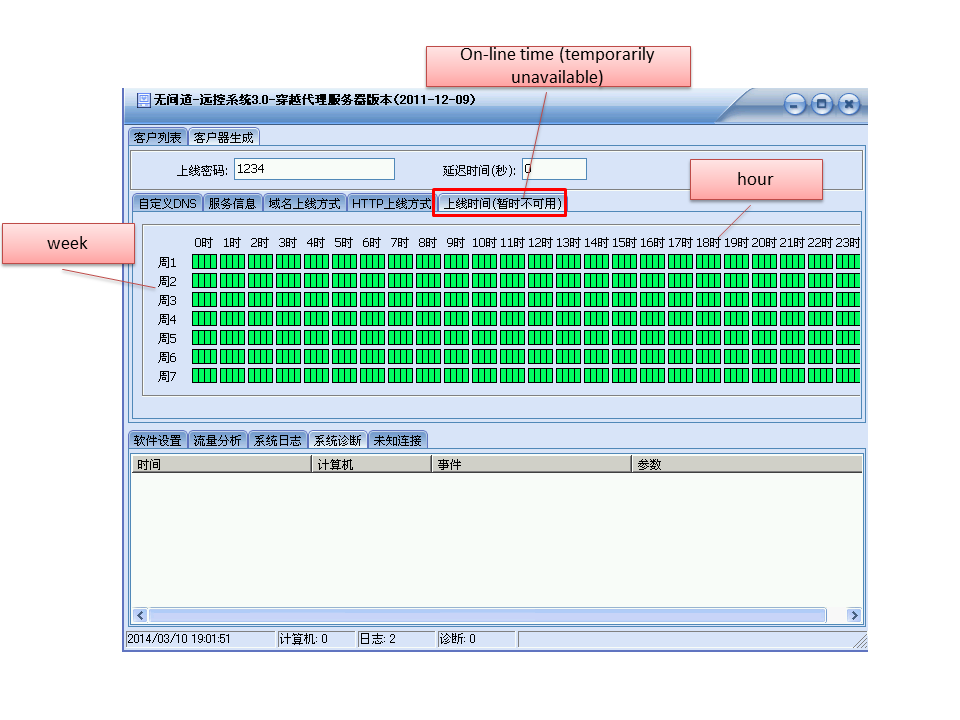
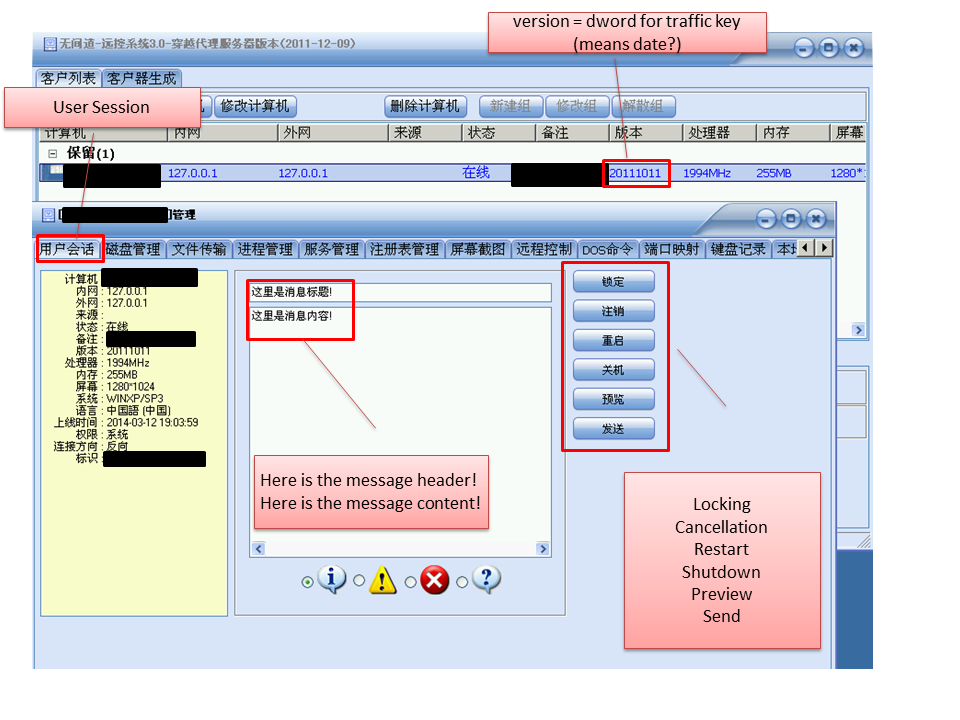
The controller also provides online status of victims.
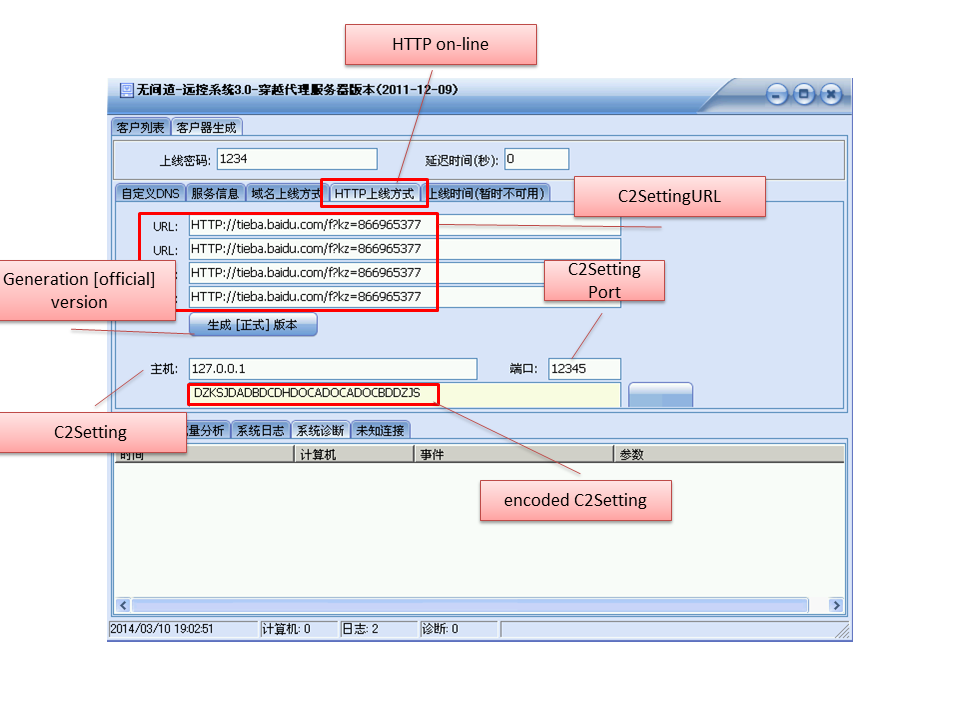
Why two “Build” buttons?
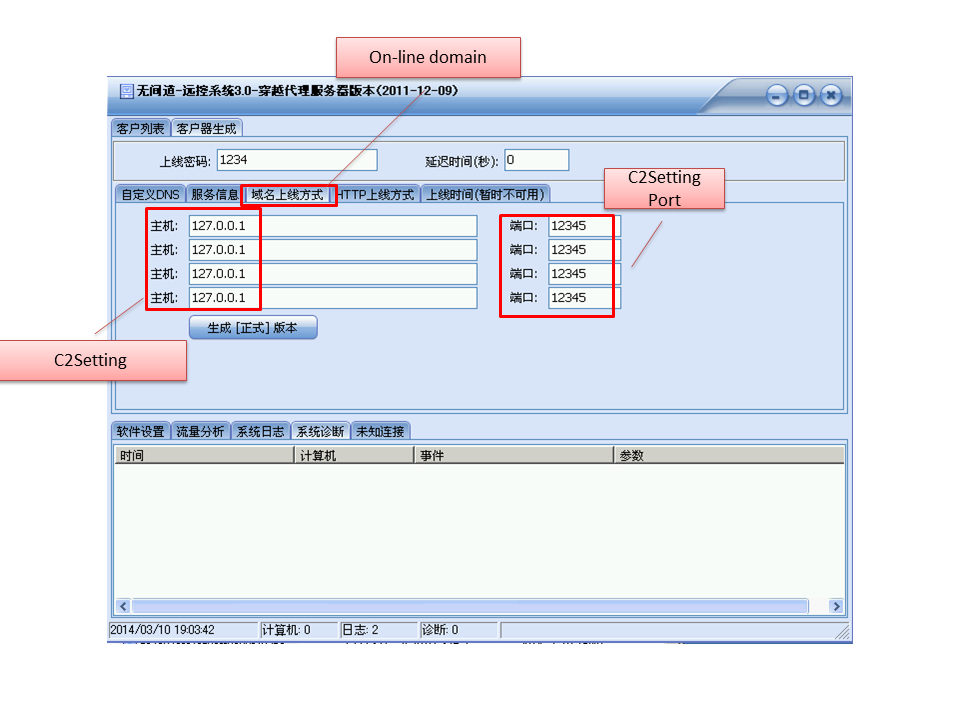
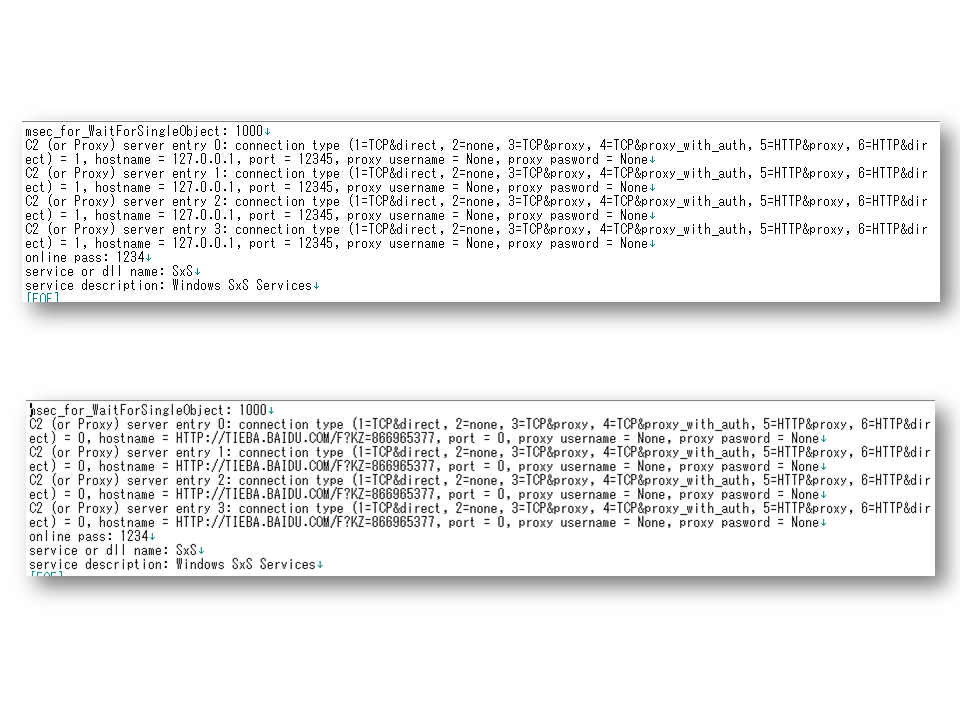
The funny thing is that there are two kinds of “build” buttons in this builder. That’s because type III specimens merge C2 setting, C2 setting URL (which is the location of DZKS/DZJS encoded file/text), proxy setting into 1 structure.
C2 setting tab
C2 setting URL tab
The built sample includes only either C2 setting or C2 setting URL. If you build in C2Setting tab, the sample includes only C2Setting information, vice versa. The size is fixed 0x840 bytes.
The config parser will be released after Black Hat Asia 2014 conference (I will also explain type I/II/III behavior, besides, co-author Hiroshi Suzuki will show the relationships between PlugX samples and attack groups)
Supported Commands
And once connected by a victim, I can open the command window.
I’m surprised RAT version is different from the controller version.
The supported commands and functions are:
- Disk Management
- File Transfer
- Process Management
- Service Management
- Registry Management
- Screenshot
- Remote Control
- DOS command
- Port Mapping
- Keylogger
- Local Log
- Remote log
The hash values
SHA256=de7a97efe1fd0aff0a90f703becc9162124ee86901a1ad57bcf5d2884c2235d2 MD5=b4d8bfb56accbd17514bffc1fa8e1953