2 years ago, I talked about the anti memory forensic method by modifying Windows kernel data structure on victim systems at BlackHat Europe 2012. The situation is still the same.
Abort Factors and PoC Driver
In the past presentation, I showed “Abort Factors”, they are key structures for virtual address translation, guessing OS version and listing kernel objects. Once they are modified, memory analysis tools cannot continue to analyze images.
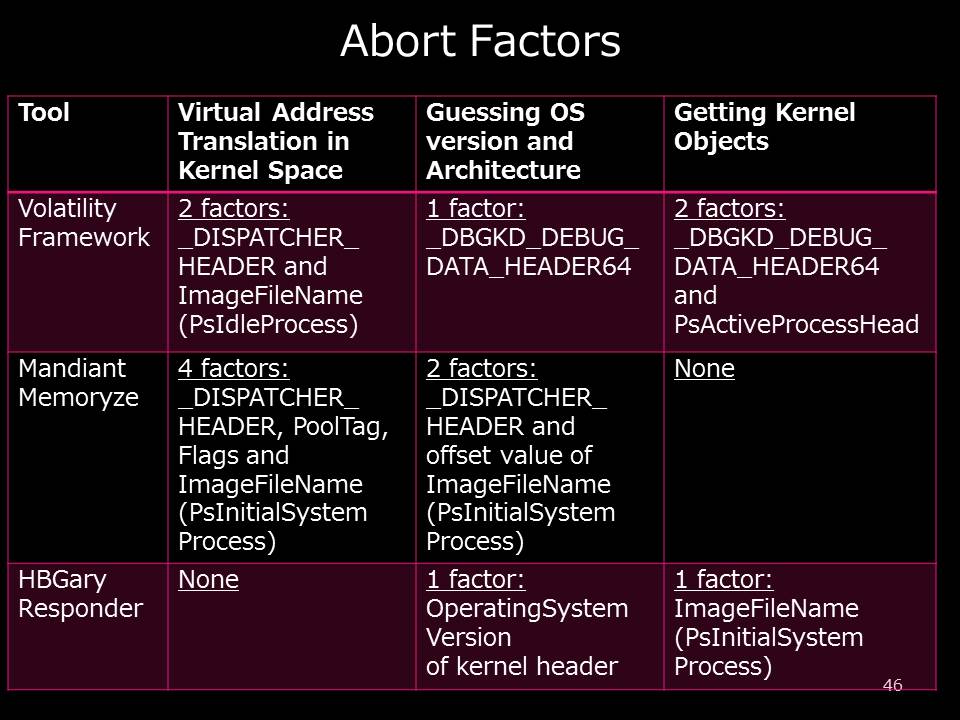
Today, I re-evaluated memory analysis tools: Volatility Framework 2.3.1 and Mandiant Redline 1.11.1 (now no one uses HBGary Responder, right?). I loaded the PoC driver modifying abort factors again then acquired the RAM. Unfortunately, the results were the same as those two years ago. I could not extract any information from the image.
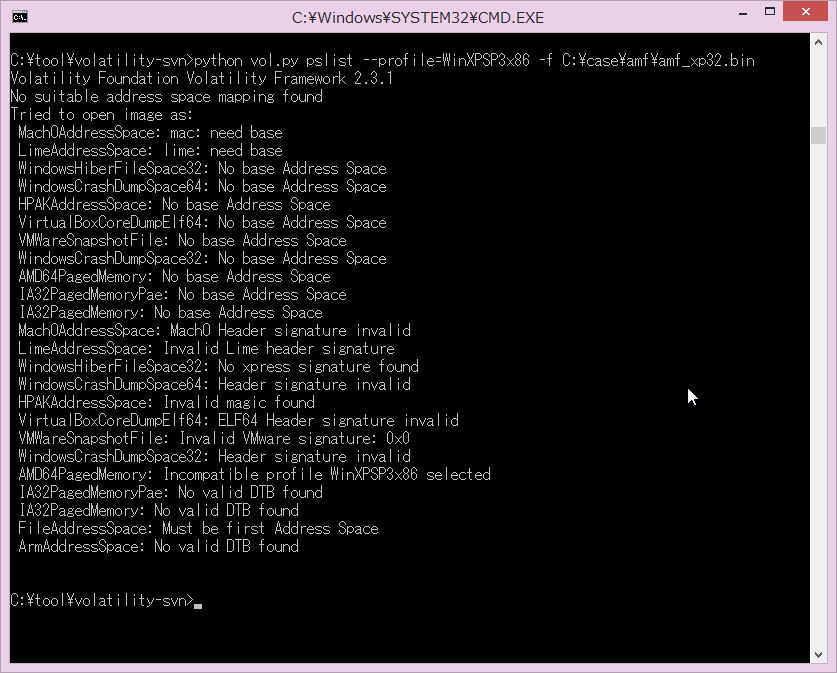
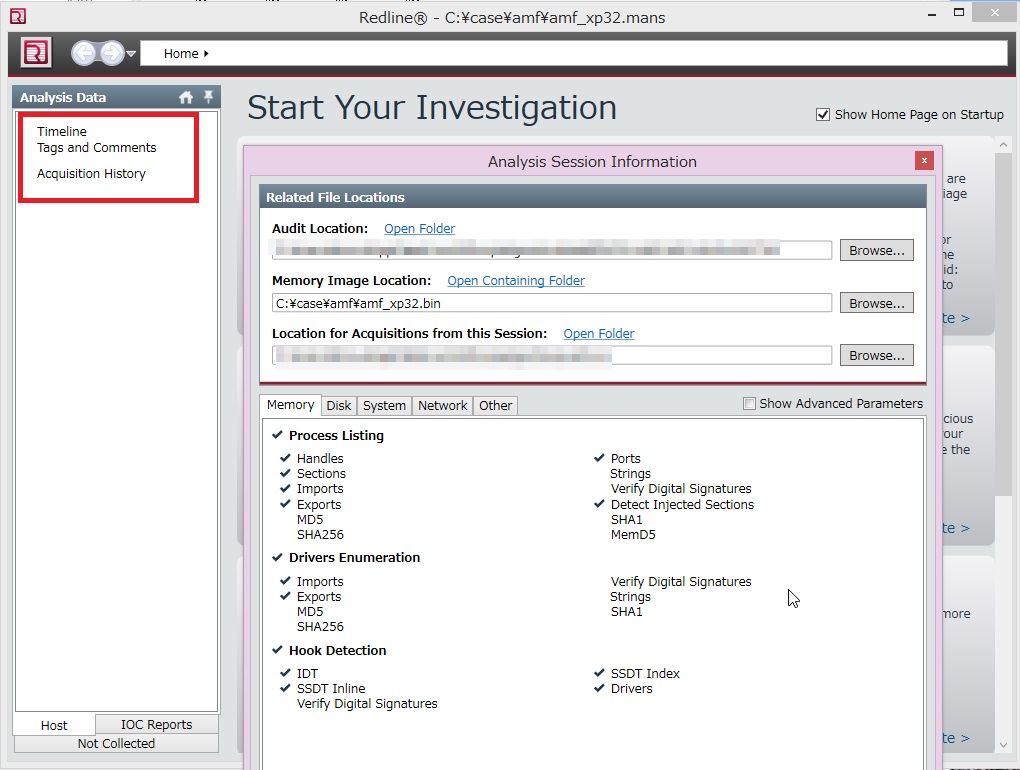
Countermeasures
As I explained in the slides, the countermeasures are simple.
The tools should keep their guessings at a minimum. For instance, support a crash dump format. A crash dump includes CR3 register value, so tools need not guess kernel DTB (Directory Table Base). If CR3 value is modified, BSOD always occurs. Besides, allow users to specify OS versions. Volatility Framework already support the options. In that sense, Volatility is better than Redline.
On the other hand, Redline (Memoryze) is better than Volatility in terms of the kernel object listing (e.g., pslist command) because it doesn’t depend on debug data structure like _DBGKD_DEBUG_DATA_HEADER64. However, Volatility users can use psscan instead of pslist. Therefore, it may be nothing more than a trivial risk.