I release Immunity Debugger and IDAPython scirpts dumping PlugX configs (and original PEs) then parsing them.
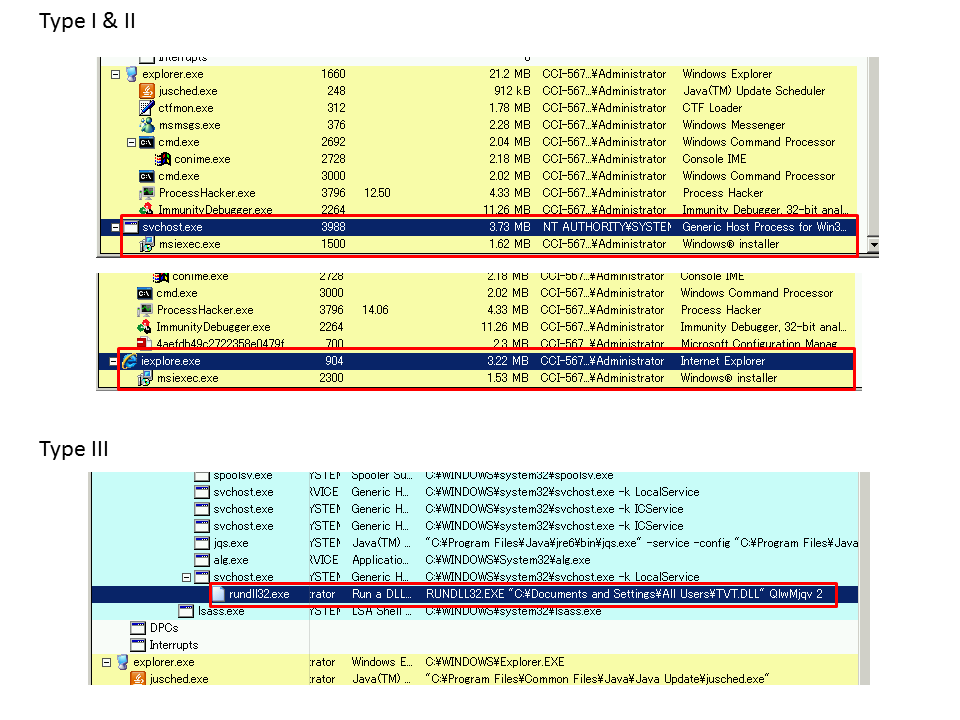
IIJ-SECT (CSIRT team at IIJ, Inc.) classifies PlugX samples into 3 types: type I/II/III. In more detail, check our presentation. The Immunity Debugger script can be used for PlugX type I&II. The IDAPython script can parse type III configs.
Distinction between Type I&II and III
Before using the scripts, we should guess which type the PlugX specimen is. Generally, type I/II injects their codes twice: the 1st target process defined in the config and msiexec. The 1st target process may be svchost/msiexec/iexplore/winlogon like the following figures. However, some samples don’t inject according to the config (stand-alone flag), additionally, other several specimens inject only once. So, the criteria is ambiguous. Moreover, in my experience, Type III is usually executed by rundll32.
ID Script for Type I&II
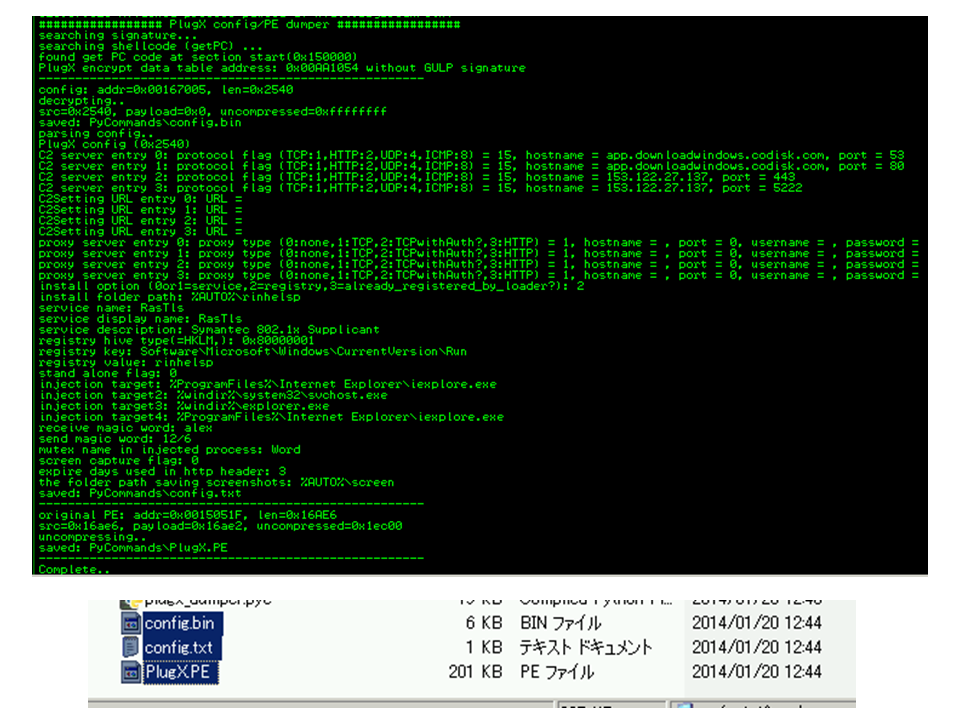
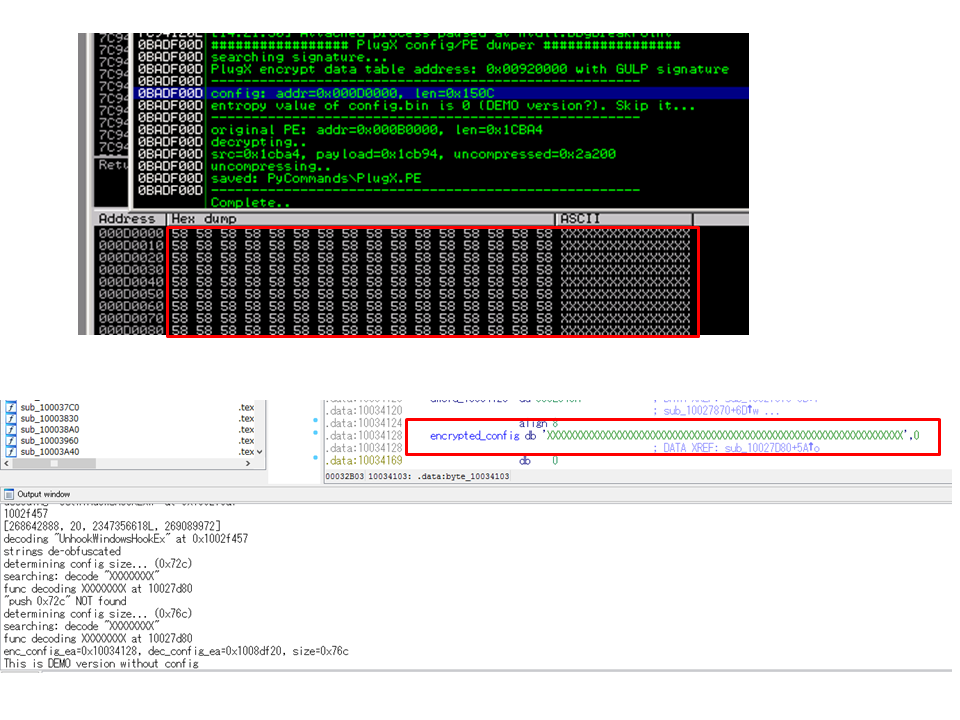
We need to copy the ID script into PyCommands folder in advance. Then we attach to one of injected processes. After attaching to the process, run the script (!plugx_dumper). If successful, the parsed config is displayed in Log View. The result and decompressed original PE file are saved in the same folder.
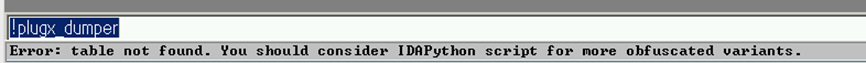
If the following message is output, the specimen may be neither type I nor II.
IDAPython Script for Type III
Since type III variants are more obfuscated (e.g., massive obfuscated strings, inserted random junk codes), it’s difficult to extract the config from process memory. Therefore, I wrote an IDAPython script for parsing type III configs.
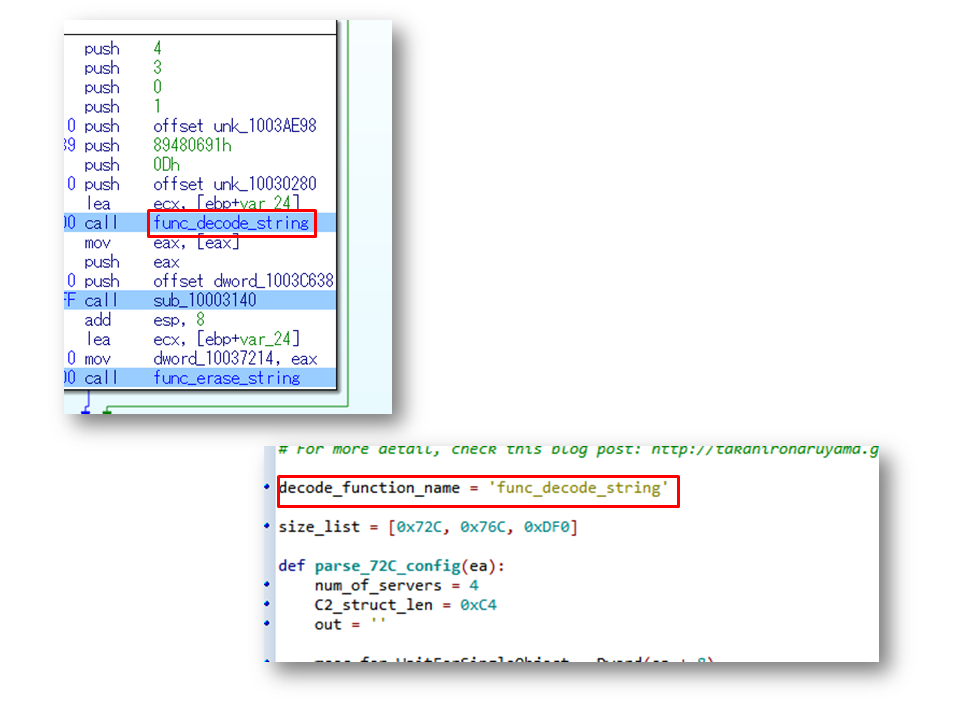
To use the script, we must find the function to decode obfuscated strings and set it as decode_function_name in the script. It may be an obstacle for DFIR people not reverse-engineering malware.
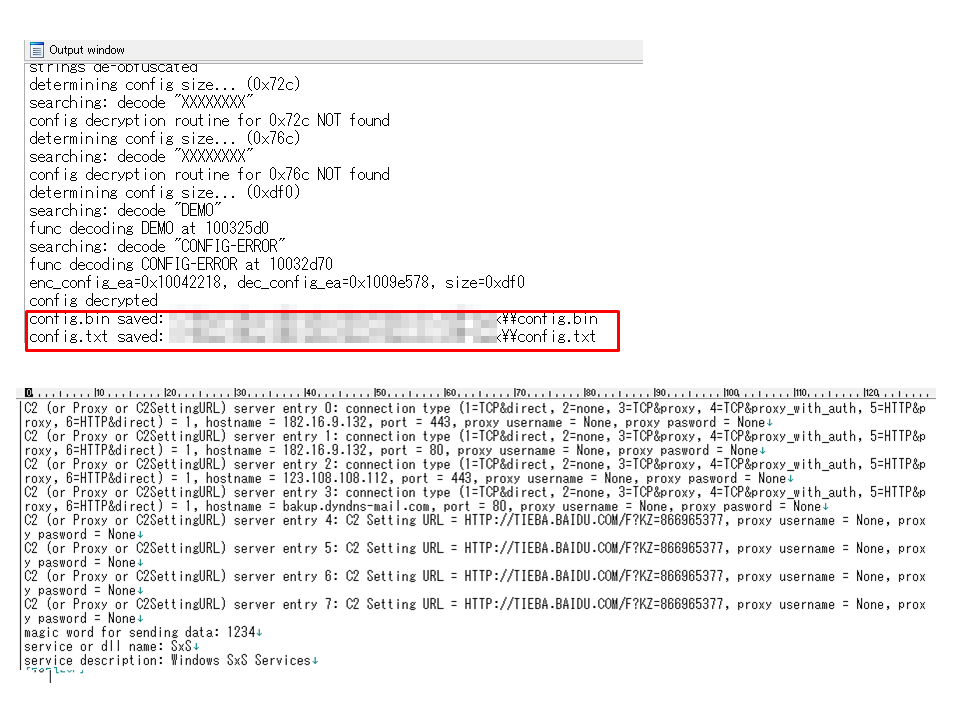
After the configuration, run the script. We can check the result in Output window. Parsed config information is saved as “config.txt”.
Note: Demo Version
PlugX demo specimens (some demo samples pop-up “THIS IS A DEMO VERSION!!!”, others not) do not include config data. When detecting the specimen is demo version, the scripts notify us of the result like this. The configs are filled by “XXXX” in demo samples.
Download
- Immunity Debugger script for type I&II (Supported config sizes are 0x150C/0x1510/0x1B18/0x1D18/0x2540/0x7AC#2)
- IDAPython script for type III (Supported config sizes are 0x72C/0x76C/0xDF0/0x7AC/0x840)
2014/4/2 updated
Immunity Debugger script output improved and 0x7AC#2 config added, that is different from Type III 0x7AC (thanks to You Nakatsuru/Arai)